Every year, our online life becomes richer: we calmly trust the provider to transmit not only passport data or card information but also medical information about ourselves. And also your location, interests, and conversations. In the same way, our personal photographs, work correspondence, and projects rush through traffic. Your whole life is in Internet connection packages. It means that it must be protected from external interference.
At the same time, the Internet has become entirely different over the past years: numerous regional blocking, semi-closed services, and other restrictions on user actions are only gaining strength. And this is the second, no less complicated task facing the user. Both of them can be solved very simply using a VPN. Today, everyone with a smartphone, computer, or game console that can connect to the Internet needs this.
Definition
VPN is an abbreviation for Virtual Private Network, “virtual private network,” denoting a generalized technology for creating a network “on top” of an existing one. Like any other computer network, global access is organized using many nodes (routers, access points, data centers), interconnected into one huge graph with a permanent or randomly assigned address at the time of connection.
Accordingly, data from the user’s computer to each resource on the Internet, be it another computer, a website, a streaming service, or any other server, passes a particular path. In the simplest case, its “traces” are divided into parts readable by the naked eye for convenient transmission. More complex ones undergo specific processing to exclude simple identification of the path traveled and the information in the packets.
In general, a VPN involves two or even three conditional operations simultaneously:
- Secure (encrypted) authentication forces the user to activate the construction of a trusted network in a certain way.
- Creation of a “tunnel”: a logically constructed sequence of connections within a global network using VPN protocols, excluding unverified nodes. The path may change randomly, making it difficult to follow. Or vice versa, save the specified configuration.
- Data encryption guarantees the safety of transmitted data with a certain probability.
Benefits of a Free VPN
Let’s start our consideration with the pros because there are many more of them than the cons.
Access to Sites from Anywhere in the World
The most apparent advantage of a VPN is that you can bypass a wide variety of blocks by using an anonymous tunnel connection. Using a direct, unknown tunnel to a server in an arbitrary country allows you to view resources blocked in your current country of residence or specific location.
Bypassing Regional Blocking of Cloud and Streaming Services
Browsing private resources is not the only widespread use of free VPN. Many content providers only offer their services in certain countries. In some cases, the same companies offer subscriptions that differ in price and content.
Secure Use of Payment Systems and Banking
Primitive schemes of scammers use direct calling and “live communication” with a person to obtain addresses, passwords, and text codes from SMS and applications.
New methods associated with the use of Trojans and social engineering make it possible to determine the availability of funds in accounts, transactions, and other system information without transmission by the user himself: modern Trojans can monitor and intercept traffic and SMS related to payments in online stores.
If a smartphone or computer uses a tunneled encrypted connection, even the most cunning methods of deception fail. Trojans are unable to leave the “tunnel,” so redirecting data traffic to attackers simply stops working. The same thing happens when scammers attempt to establish a connection to remotely control a smartphone or computer.
Blocking Phishing Attacks
Thanks to tunneling, it is always difficult for attackers to carry out a targeted phishing attack: additional encryption of such resources makes traffic monitoring difficult.
This way, fraudsters cannot link information about purchases or payments for other services to the specific device on which it was made. And they will be unable to carry out a targeted attack, a “hot call.” They simply will not have the initial data so often used in such crimes. And “hitting the area” is too expensive for them. Hidden VPN devices and resources are the least likely to be targeted by phishing.
Security of Transmitted Data
Most VPN services are able to actively practice complex data encryption methods in stream mode on the fly. You can organize this yourself, but not every user can handle it.
For those who are particularly concerned about their privacy, it may be beneficial to use more advanced tunnel access resources that can replace or mask DNS servers, “mix” user traffic, or utilize distributed access to external resources.
Cons of Free VPN
Free services have not only advantages but also disadvantages. To maintain objectivity, let’s analyze the opposing sides of these tools:
- Unstable quality. The range of services and their quality greatly depends on the chosen service. You may encounter low-quality services or even become a victim of scammers. Therefore, it is essential to select a free service carefully.
- Paid services may be available. Often, such services are only conditionally free. A limited number of locations may be available to you, and you will need to pay to connect the rest. The same applies to some functions. Check out the functionality available for free.
Thus, it all depends on how responsibly you take the selection of a VPN. A free service can be reliable and of high quality, but there is a risk of running into scammers.
Conclusion
A VPN is a convenient tool that allows you to access various resources while protecting your data. It is not necessary to use paid services. A free VPN can be just as reliable and convenient. The main thing is to choose the right service.


 How to Choose the Right GenAI Partner for Your Business in 2026
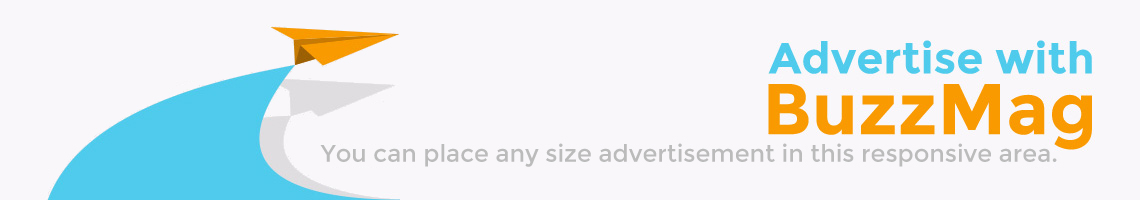
How to Choose the Right GenAI Partner for Your Business in 2026  Practical Strategies for Building Reliable Network Security in a Cloud-First World
Practical Strategies for Building Reliable Network Security in a Cloud-First World  DeepSeek R1: The AI Revolution That Defied U.S. Trade Barriers and Stunned the World
DeepSeek R1: The AI Revolution That Defied U.S. Trade Barriers and Stunned the World  Why Some AI Models Fail Under Pressure – A DeepSeek AI Case Study
Why Some AI Models Fail Under Pressure – A DeepSeek AI Case Study  Various Ways to Sell Bitcoin for Cash Instantly
Various Ways to Sell Bitcoin for Cash Instantly  Understanding the Fundamentals of Intrusion Prevention Systems
Understanding the Fundamentals of Intrusion Prevention Systems