Security is vital for digital products and services, and customers expect them to be secure, especially when incorporating them into their own services. A manufacturer using a sensor in product design hopes it’s not vulnerable to cybersecurity threats due to its customers’ reliance on its security. Cyberattacks on devices connected to the internet can create an entry point for hackers to access internal systems, steal confidential data, plant malware, or collect sensitive data. Regrettably, well-publicized breaches show development efforts have fallen short in securing digital offerings.
When developing digital products or services, security is crucial and must be integrated during the initial design stage to ensure safety and lower costs. In practice, security is only an afterthought, addressed after product design, but preparing for it early helps follow customer expectations.
Although traditionally all cybersecurity issues are assigned to the IT department, all employees are at risk. Anyone who passes user authentication not from the workplace can become a source of viruses and data interception. Designers greatly underestimate how often they become the target of attacks.
As a designer, you face various cybersecurity threats daily. This is especially true for freelancers and remote workers. Working remotely and as a freelancer has increasingly gained popularity. In the US, over 13 million individuals joined the industry between 2017 and 2022, increasing the total to over 70 million. This number is expected to reach 90 million by 2028. We are here to discuss secure design principles and suggest ways to help protect your company from cyber threats.
Why is cybersecurity always in trend?

If you spend enough time online, you’re bound to encounter a virus or phishing attempt. Good practices and antivirus programs can protect you, but when you zoom out, it’s clear that organizations face much bigger security challenges, such as outdated or unprotected software, unaware staff, and a lack of vigilance.
The biggest cyber attacks in history, such as Red October, WannaCry ransomware attack, and NotPetya cyberattack, still have consequences today.
These cyber-attacks have demonstrated that governments, companies, and individuals are vulnerable to cyber threats unless they are aware of them and their potential damage. It’s shocking that WannaCry and other viruses have caused an estimated $10 billion in damages! And it’s not just WannaCry. Attacks on digital infrastructure are increasing, like the ones on water treatment plants.
Cybercriminals look for weaknesses in software, such as unpatched VPNs, SQL injections, cross-site scripting, server misconfigurations, and sensitive data being displayed in plain text. In addition to applications, phishing and similar scams that exploit genuine credentials are the preferred means for hackers to access restricted software.
But there’s good news! When the design and development team prioritizes security from the beginning, it creates practices and standards that keep users and their data safe, while blocking hackers’ attempts to attack.
Cybersecurity Best Practices for Designers
#1 Cloud storage
As a remote worker, you may handle sensitive client data. To securely store and manage these files, many use cloud storage. This allows for seamless editing, sharing, and synchronization. However, not all cloud storage services are safe. Using a vulnerable one can lead to stolen or corrupted data. Therefore, invest in a trusted, fully secure option to protect your valuable information.
Cloud storage services like Google Drive and OneDrive are typically secure, but using specialized providers with security as a top priority is an option. Examples include Sync, Tresorit, pCloud, Mega, and IceDrive.
#2 Minimize the area of attack
As you add more features like webpages or network protocols to your product or system, its attack surfaces and the vulnerable areas where attackers could strike get bigger too. Each new feature opens up new ways for cybercriminals to take advantage. This means, as time goes on and you integrate more products or systems with your own, the security risk for your product or system also goes up.
From a security standpoint, it’s crucial for organizations to find ways to minimize the attack surface area as much as possible. This is where cyber secure development comes into play, as it proactively reduces the attack surface of a product or system when making changes. This only at first glance does not apply to designers. To a large extent, this affects all employees and designers of any form of employment too.
To improve security:
- reduce the number of user roles;
- don’t store confidential data that isn’t essential;
- disable features that aren’t needed or not needed all the time;
- include operational controls, such as Web Application Firewalls (WAF) and other intrusion detection and prevention systems.
#3 Protect offline data
If you’re saving work-related data on personal devices like a laptop, phone, or tablet, it’s important to encrypt that information. Popular operating systems like Windows and iOS have built-in encryption tools, or you can buy hardware-encrypted storage devices to protect your data. Plus, backing up your important files regularly can help you recover from any unexpected data loss.
#4 Choose secure communication tools
If you are still using WhatsApp General Chat, you are outdated. There are specialized corporate solutions for internal communications. Even the same Telegram offers a good level of privacy, but it is better not to use it to send important data.
To do this, there is an old and proven technology for sending and receiving documents – fax. With it, secure file sharing is possible at any distance. If you think that faxing is inconvenient due to being tied to a fax machine, then there is a solution. Now there is a Fax apple that can do everything the same as landline fax and even more. Digital fax is useful because it can scan, send and receive documents while maintaining a standard format. You don’t have to worry about possible formatting difficulties when sending, they all work according to the same standards. This is one of the simplest ways to organize privacy by design.
#5 Keep your environment updated
Did you know that there might be many hidden ways that others can enter your computer’s operating system and daily used programs? But don’t worry, developers are always finding and fixing the issues which could lead to hacks and exposing confidential information.
Adhere to the following tactics to keep your software as secure as possible.
- Make sure to keep all of your software up to date, including your operating system, browser, antivirus, and any other programs you use regularly.
- Most software programs have the option to enable automatic updates, which can help ensure that your software is always up to date.
- If you don’t have automatic updates enabled, then make sure to check for updates regularly. You can usually do this through the software’s preferences or settings menu.
- Once updates become available, it’s essential to install them immediately to help keep your system secure.
#6 Use a firewall/antivirus
Cybercriminals are notorious for designing malware and viruses with malicious intent. These can not only cause data corruption but also lead to the theft of your private information, including payment or freelance account credentials.
It’s important to safeguard your device against such threats by installing a reputable antivirus solution and enabling a firewall. Whether you’re using Windows, iOS, or Linux, make sure to take these preventive measures on the device you use for freelancing.
You can use Norton, McAfee, Bitdefender, and Kaspersky as some of the best antivirus options that come packed with integrated firewalls, which act as a second line of defense that protects your device from harmful cyberattacks. Additionally, it’s highly advisable to install an antivirus app on your work smartphone as well. Surprisingly, statistics indicate that only 24% of smartphone users have an antivirus tool installed compared to 70% of computer users.
According to the report, viruses can affect both computers and phones alike. Hence, it’s important to have an antivirus app installed on your smartphone too. The antivirus options mentioned earlier are available for both iOS and Android devices.
#7 Use security browser plugins
As a designer, an internet browser is a tool you shouldn’t go without. You use it to browse for inspiration for your projects, stay updated with the latest design trends by reading design blogs, search for new job opportunities, and communicate with clients. However, many websites contain malware that can infect your device. This could give hackers unrestricted access to your device.
Most of the popular internet browsers such as Google Chrome and Mozilla Firefox are equipped with useful security plugins. These plugins are lightweight and won’t impede your browsing speed. Additionally, they prevent malware attacks and protect your device while browsing. However, make sure to install trusted browser extensions only, as they can have intrusion and malicious behaviors.
#8 Use only trusted payment platforms
As a freelance designer, you’ll be accepting payments from clients located all over. Choose a secure payment platform so you can accept payments without any hassle. Don’t forget to check the payment gateway for safety!
Don’t fall into the trap of relocating your conversation or working away from reputable marketplaces like Upwork and Fiverr. Avoid accepting payments from unverified platforms, and exercise caution when communicating with clients or submitting work through email or messaging apps. These steps will lower the chances of falling prey to cyber attacks, theft of important information like payment and design details, and risks to one’s credentials and identity.
You can trust platforms like PayPal, Wise, and Payoneer. If you want to use a different platform, follow these tips to ensure safety and security.
- Make sure to search for reviews and also ask other freelancers or business owners for recommendations.
- Don’t forget to look into the platform’s security measures to discover which protocols they use.
- Make sure that the platform uses features such as encryption, fraud protection, and two-factor authentication.
- Finally, ensure to read and grasp the payment platform’s associated fees as well as any terms and conditions.
It’s a good idea to give your clients various payment options, including credit cards, debit cards, e-transfers, and bank transfers. This not only makes it simple for them to pay but also protects you in case one payment method is at risk.
#9 Protect yourself from public Wi-Fi networks
Thanks to advancements in machine learning and artificial intelligence, bad actors no longer need to do all the grunt work themselves. Instead, they develop bots powered by AI to scour the internet for vulnerable devices to break into.
Using a public network places your device at risk and makes it an easy target for these bots. So, when possible, avoid using public networks and set your device to not automatically connect to available public internet connections.
If you ever have to use public Wi-Fi, make sure you protect yourself before logging on. First, check that your firewall is on and that your antivirus is running. Also, using a VPN will encrypt your online data transmission making it almost impossible for hackers to steal sensitive information.
It’s also crucial to install a VPN tool like VeePN on your device, which will hide your physical location by routing your IP address through a server in a distant area. That way, it’ll be harder for cybercriminals to target your device.
#10 Take care of password security
Creating strong passwords is crucial to safeguarding your freelance and payment accounts’ first line of protection. Here are some tips for creating and managing strong passwords:
- Using a password manager like LastPass can help you create and store unique, strong passwords for all your accounts, and you can manage them in one place.
- Enabling two-factor authentication (2FA) involves an additional step to log in, such as receiving a code sent to your phone or email. It adds an extra layer of security and can prevent unauthorized access even if someone else has your password.
- Make them complex: A mix of upper and lower case letters, numbers, and special characters like !, @, #, or $ can make your password more difficult to guess.
- Use longer passwords: Longer passwords are stronger and more secure than shorter ones. Whenever possible, aim for at least 12 characters.
- Avoid personal information: Don’t use personal information like your name, address, or birthdate in your password.
- Use a unique password for each account: Using a different password for each account can help protect you against unauthorized access if one password is compromised.
#11 Use VPN everywhere, outside of work and at home
A VPN means you’re browsing privately. It’s like a shield that makes your online activities anonymous and confidential by creating a secure path over the internet. You can use this service when you’re working from a location outside your home or office. This service encrypts everything you do, which protects you from unwanted attention on public Wi-Fi networks and more. The provider can also monitor your actions. but a VPN solves this problem.
#12 Manage access rights
Managing access rights helps ensure that each person can access the resources they need to do their job well. This will be useful if you’re working with a team of freelance designers. For example, let’s say you have three projects – A, B, and C – and you’ve stored related data in your cloud storage. You then create three teams, one for each project – X, Y, and Z.
If a team is working on a project, they only need access to the data they’re working on. For that, you need to manage access rights so each team can view and use just the data they need. If you’re working alone, managing access rights will help you keep client information and account credentials private. No one else needs to know this information, only you.
#13 Stay up to date with the latest cyber threats
It’s crucial to keep informed about the latest cybersecurity risks and scams to safeguard yourself, and your clients, and anticipate potential threats. A number of newsletters and industry publications, like Gartner and Security.org, cover cybersecurity and highlight the most recent threats and scams. By subscribing to these resources, you can stay aware of what to look for. You could also follow cybersecurity specialists and organizations on social media platforms, such as Twitter, LinkedIn, and Facebook, to receive information on threats and scams.
#14 Attend cybersecurity events
Attending industry events and conferences is a great way to update yourself on the latest threats and scams in the field. You’ll even have a chance to learn from experts and meet other professionals in the industry. Don’t forget to enroll in cybersecurity training programs too! These programs will improve your skills and keep your knowledge current.
#15 Follow security documentation
Having proper documentation is crucial and shouldn’t be overlooked when it comes to security. The documentation must cover the entire product lifecycle and should be prepared by the team responsible for designing and developing the said product. There are three types of documentation: internal, maintenance, and end-use.
The documentation for internal use should explain the product thoroughly, allowing OEMs to enhance or debug the product and spot cybersecurity gaps. Every member of the team, the designer in particular, should have access to it and also have an idea of the key positions in the document. OEMs keep this documentation, which should cover but not be restricted to the following:
– All functions
– Used technologies
– High-level and detailed design
– Software and hardware architecture
Maintenance documents must provide specific information to help and support supervisors, and field or maintenance engineers to safely deploy or commission a product. Such documentation must cover installation and configuration processes, secure deployment and commissioning, troubleshooting guidance, and update/upgrade processes.
The documentation designed for end users should concentrate on the secure use of the product throughout its life cycle. The aim of this documentation is to guide end users in using the product in a secure environment and in securely disposing of it at the end of its life cycle. This documentation should be straightforward and easily obtainable and made available either along with the product or on the manufacturer’s website. The end-user documentation must include a variety of aspects like security hardening guidance, firewall rules, secure decommissioning procedures, and other specific instructions as necessary.
#16 Integrate cybersecurity into the design
To ensure cybersecurity, it’s crucial to integrate it into product and service design from the start of technology projects. Large organizations often have formal governance processes to support software development that includes cybersecurity reviews at various stages of the development lifecycle, as well as vulnerability testing after development is complete.
The issue is that when security problems are found towards the end of product development, they can put the project on hold. Then, incorporating security features may require a costly redesign that could have been avoided if they were considered from the start. By making cybersecurity part of the initial design, organizations can avoid these issues and keep up with the demands of digital transformation.
#17 Complementary responsibilities
Beginning the design process with cybersecurity is vital, but it requires a complete shift in mindset regarding how design and cybersecurity teams work together. Usually, product teams concentrate on developing amazing products and features and tend to regard cybersecurity as an obstacle to be surmounted or entirely avoided in some cases. Meanwhile, cybersecurity teams manage general risks to enterprise computers and evaluate the risks that come with the end product in this context.
To make sure that new products and services are secure against online threats, cybersecurity, and design teams should work together. Cybersecurity staff must provide advice and support for security design and architecture, bringing in new abilities and skill sets. This requires a culture of teamwork, a service mindset, and the capability to offer guidance on cybersecurity design – not just simply checking if security standards and practices are met.
Product development teams need to be detailed about their products or service requirements to team up with cybersecurity members. The evaluation of complex systems’ cybersecurity posture is difficult. Yet, understanding how they work helps determine what set of controls are needed. Working alongside cybersecurity colleagues, product teams can succeed by identifying crucial components for the project and potential failure outcomes.
Conclusion
As we can see, cybersecurity is an important factor to consider in the realm of digital design. Not only do designer-incorporated security measures strengthen customer trust, but they also go a long way in ensuring data protection for both clients and users. Being knowledgeable about cybersecurity basics can guard against the risks that threaten sensitive data, finances, and even websites themselves.
Designers must also keep up with the challenges of the digital world. To prevent them from being a weak link in the entire cybersecurity system, the strategies described above should be followed. Employing these strategies can bring peace of mind knowing your materials are secure and enhance user confidence in the process. In the end, it’s worth taking the extra steps needed for optimal protection so you can continue designing with ease and safety always in top-of-mind.


 How to Choose the Right GenAI Partner for Your Business in 2026
How to Choose the Right GenAI Partner for Your Business in 2026 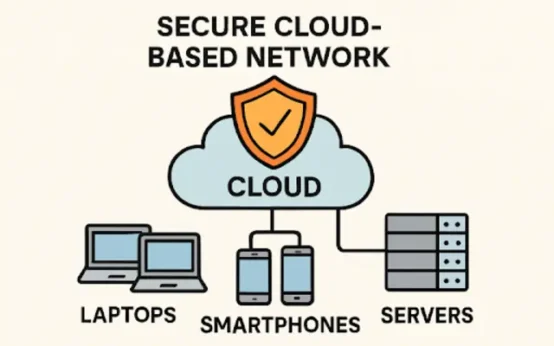 Practical Strategies for Building Reliable Network Security in a Cloud-First World
Practical Strategies for Building Reliable Network Security in a Cloud-First World  DeepSeek R1: The AI Revolution That Defied U.S. Trade Barriers and Stunned the World
DeepSeek R1: The AI Revolution That Defied U.S. Trade Barriers and Stunned the World  Why Some AI Models Fail Under Pressure – A DeepSeek AI Case Study
Why Some AI Models Fail Under Pressure – A DeepSeek AI Case Study  Various Ways to Sell Bitcoin for Cash Instantly
Various Ways to Sell Bitcoin for Cash Instantly  Understanding the Fundamentals of Intrusion Prevention Systems
Understanding the Fundamentals of Intrusion Prevention Systems